Emotet Spam Campaign: A Persistent Cyber Threat
The Emotet malware, once dubbed the “most dangerous malware in the world,” has been wreaking havoc since its discovery in 2014. Initially a banking Trojan, it has evolved into a sophisticated, multi-purpose threat capable of facilitating large-scale cyberattacks. One of Emotet’s primary infection vectors is through spam email campaigns, which continue to target businesses and individuals worldwide.
In this blog post, we’ll dive into what the Emotet spam campaign entails, how it works, and what can be done to mitigate the risks associated with this malicious software.
What Is Emotet?
Emotet started as a Trojan designed to steal financial information, such as banking credentials, by intercepting data during transactions. However, over time, it evolved into a powerful malware-as-a-service (MaaS) platform. It now serves as a delivery mechanism for other types of malware, such as ransomware (e.g., Ryuk) and information stealers (e.g., TrickBot).
This evolution has made Emotet a favorite tool among cybercriminals looking to launch multi-stage attacks, leveraging its botnet infrastructure to distribute malicious payloads to compromised machines.
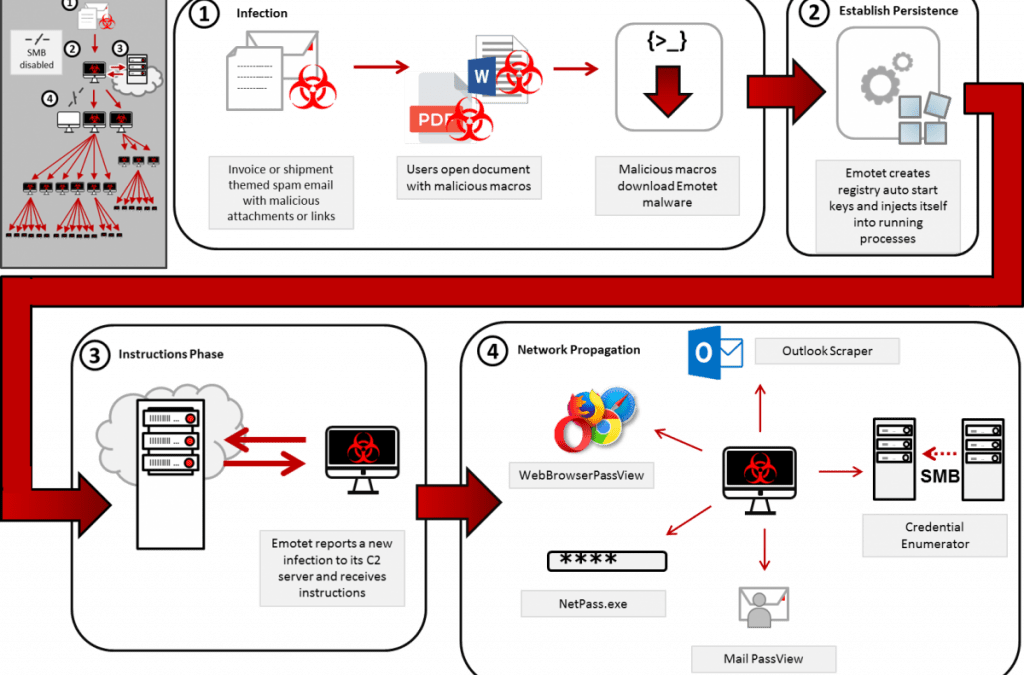
The Emotet Spam Campaign: How It Works
The Emotet spam campaign typically begins with phishing emails designed to trick recipients into opening a malicious attachment or clicking on a link. These emails often appear legitimate, masquerading as trusted sources such as banks, government institutions, or well-known companies.
Here are the key methods that attackers use in Emotet spam campaigns:
Malicious Attachments: Emails may contain Word documents, PDFs, or Excel files that include malicious macros. When the recipient downloads and enables the macros (often through deceptive instructions), the malware is installed on the system.
Embedded Links: Some emails will include links that lead to compromised websites or fake download pages, which install the Emotet malware onto the victim’s machine.
Thread Hijacking: A particularly effective technique used by Emotet is hijacking legitimate email threads. By gaining access to compromised accounts, Emotet replies to existing email conversations, adding a malicious attachment or link. This increases the likelihood of the recipient trusting the message and clicking the link.
Social Engineering Tactics: Emotet emails are often crafted with urgency, playing on common themes such as unpaid invoices, overdue payments, or missed deliveries. The goal is to prompt the victim to act quickly, overriding any caution about opening attachments or clicking links.
The Dangers of Emotet
Once a system is infected with Emotet, the malware can download additional payloads, including:
- Banking Trojans: Designed to steal financial information.
- Ransomware: Encrypts files on the victim’s computer and demands payment for the decryption key.
- Credential Stealers: Harvests login credentials, which can then be sold on the dark web or used for further attacks.
Additionally, Emotet is notorious for spreading laterally across networks, infecting other devices and escalating the impact of an attack. Large-scale Emotet infections can lead to widespread data breaches, financial losses, and operational disruption for businesses.
How to Protect Against Emotet Spam Campaigns
As Emotet continues to evolve and adapt, it remains a formidable threat. However, there are several measures individuals and organizations can take to protect themselves:
Employee Training: Educate employees about phishing tactics and encourage them to scrutinize emails, especially those with attachments or links, even if they appear to come from trusted sources.
Disable Macros by Default: Ensure that macros are disabled in office documents by default. Most users do not need to enable macros for daily tasks, and disabling them can block a significant vector of attack.
Email Filtering: Implement an advanced email filtering solution like SpyderMail Email Security that can detect and block malicious attachments and links before they reach users’ inboxes.
Regular Patching and Updates: Ensure that all systems, including software and security tools, are regularly updated. Cybercriminals often exploit unpatched vulnerabilities in outdated systems.
Endpoint Protection: Deploy and maintain up-to-date endpoint protection solutions capable of detecting and neutralizing malware before it can execute.
Network Segmentation: Segment your network to limit the spread of malware should an infection occur. This helps contain the damage and prevent lateral movement.
The Emotet spam campaign continues to be a major cybersecurity threat, especially given its adaptability and use in distributing various forms of malware. By understanding how Emotet operates and taking proactive steps to secure your systems, you can significantly reduce the risk of falling victim to this malicious campaign. Stay vigilant, keep your software updated, and educate your team to ensure they recognize the red flags of a phishing email.