Understanding CryptoLocker: The Infamous Ransomware Threat
CryptoLocker is one of the most notorious ransomware strains in cyber history. First appearing in late 2013, this malicious software quickly gained attention for its aggressive encryption techniques and high ransom demands. CryptoLocker targeted Windows computers, encrypting files and rendering them inaccessible until the victim paid a ransom, typically in Bitcoin. Although the original CryptoLocker was disrupted in mid-2014, its impact on cybersecurity and the ransomware landscape has been long-lasting.
In this blog post, we will explore how CryptoLocker operated, the damage it caused, and the lessons it left behind for both individuals and businesses.
What Is CryptoLocker?
CryptoLocker is a type of ransomware, a malicious software that encrypts a victim’s files and holds them hostage until a ransom is paid. The ransomware primarily spread through phishing emails containing malicious attachments, often disguised as harmless files like PDFs or Word documents. Once the victim opened the attachment, the ransomware would install itself on their computer, search for specific file types, and begin encrypting them using strong cryptographic algorithms.
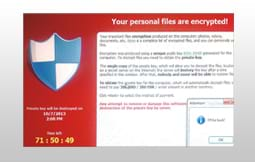
After encryption, CryptoLocker would display a ransom message, demanding payment in exchange for the decryption key. Victims were typically given a short deadline (usually 72 hours) to pay the ransom, after which the price would increase or the decryption key would be permanently destroyed, leaving the files unrecoverable.
How CryptoLocker Worked
-
Infection Vector: The primary method of infection was through phishing emails. These emails tricked users into downloading and running the ransomware by pretending to be from trusted sources, such as postal services or legitimate businesses. Once opened, CryptoLocker would silently install on the system.
-
File Encryption: CryptoLocker used advanced encryption methods, typically RSA-2048 and AES-256, to encrypt files on the victim’s computer. It targeted common file types, including documents, images, spreadsheets, and other data files that would be valuable to the user.
-
Ransom Demand: Once the files were encrypted, CryptoLocker displayed a message informing the user that their files were inaccessible and demanding a ransom, usually between $300 to $500 in Bitcoin or prepaid cards. The message included a countdown timer, warning that the price would double after the deadline or that the decryption key would be destroyed if the ransom was not paid.
-
Decryption Key: CryptoLocker’s encryption relied on a public-private key pair, where the private decryption key was stored on the attacker’s servers. Without this key, it was impossible to decrypt the files, making paying the ransom the only way for most victims to regain access to their data.
-
Propagation: Though initially targeted at individual users, CryptoLocker soon spread to corporate networks. Once installed on a computer, it could propagate through shared network drives, infecting more machines and encrypting data across an organization.
The Damage Caused by CryptoLocker
CryptoLocker caused widespread devastation, both to individuals and businesses. Victims who did not have up-to-date backups were often left with little choice but to pay the ransom. According to reports, the attackers behind CryptoLocker extorted millions of dollars from victims, making it one of the most financially successful ransomware campaigns of its time.
Several high-profile cases of businesses losing critical data to CryptoLocker gained media attention, highlighting the dangers of ransomware and the importance of proper cybersecurity measures. Even though law enforcement eventually dismantled the botnet responsible for spreading CryptoLocker, variations of the ransomware continued to appear.
The Takedown of CryptoLocker
In mid-2014, a joint effort by law enforcement agencies and cybersecurity firms led to the takedown of the Gameover Zeus botnet, which was used to distribute CryptoLocker. This operation, called “Operation Tovar,” significantly disrupted CryptoLocker’s distribution network and led to the seizure of the servers storing the decryption keys.
Shortly after the takedown, cybersecurity researchers released a free decryption tool that allowed victims to recover their encrypted files without paying the ransom. While the original CryptoLocker threat was neutralized, the tactics and techniques it introduced have been replicated by other ransomware strains, continuing to pose a threat.
Lessons Learned from CryptoLocker
CryptoLocker served as a wake-up call for many organizations, emphasizing the need for robust cybersecurity defenses. Some key lessons from the CryptoLocker outbreak include:
-
Backups Are Critical: One of the most effective ways to defend against ransomware is by maintaining regular backups of important data. Backups should be stored offline or on separate networks to prevent ransomware from encrypting them as well.
-
Phishing Awareness: Since phishing emails were the primary infection vector for CryptoLocker, user education and awareness are crucial. Employees should be trained to recognize and avoid suspicious emails, links, and attachments, with one of the best training being KnowBe4.
-
Up-to-Date Security Software: Keeping antivirus and anti-malware software up-to-date can help detect and block ransomware before it infects a system. Regular patches and updates to operating systems and software are also critical to closing security vulnerabilities.
-
Network Segmentation: Isolating critical systems and data from the broader network can help contain the spread of ransomware and reduce the risk of large-scale infections.
CryptoLocker was one of the earliest and most significant ransomware attacks, marking the beginning of a new era of cybercrime. Its aggressive encryption and ransom demands set the stage for the many ransomware threats that followed. While the original CryptoLocker has been neutralized, ransomware continues to evolve, making it more important than ever for individuals and organizations to prioritize cybersecurity.
By implementing strong defenses, such as regular backups, phishing awareness, and up-to-date security software, you can reduce the risk of falling victim to future ransomware attacks.